Ian Ardouin-Fumat, Karyn Pugliese, and Shivangi Dave
Background & Research:
Initial concept
Street protest is a potent form of dissent, used across history and geography as a tool for progress and social justice; it directs public attention and persuades political actors to change course. In this way, while protests are subversive, they are also integral to democracy in expressing opinions, desires and demanding accountability. As noted by Mols Sauter in The Coming Swarm (2014) if civil disobedience and disruptive activism are valuable tools of activist speech and political discourse in the physical world, then it must also be acknowledged that they should be equally valuable and desirable in the online space.
Protest events in the physical world have become compromised by the COVID-19 pandemic and the global quarantine experienced all over the world. However, while it may no longer be safe to protest on the street, the causes that inspire activism have not gone away – the climate emergency, undocumented people, the struggle of women and victims of domestic violence, the labor rights of essential workers, and the protection of ordinary citizens against government surveillance.
Some activists have gone online, using hashtags, attempting to make viral videos, use phone mobbing or other techniques to draw attention to causes. (Shola Lawal “Coronavirus Halts Street Protests, but Climate Activists Have a Plan” in The New York Times, March 19, 2020) In Russia, activists created a virtual traffic jam using Yandex. Christopher Miller “Protest So They’ve Gone Online. But They’ll Be Back” BuzzFeed, April 25, 2020)
However, these protests lacked an important element of disruption. The hashtags and videos are easily ignored by those in power, Yandex erased the protestors pins saying they had nothing to do with traffic reports, which is the purpose of the app.
But if there’s no public space on contemporary internet, how do we facilitate dissent and uncomfortable conversations?
As patience fell with social distancing, the forced shut down of non-essential businesses and related economic impact due to Covid-19; some real-life protests have erupted. (Nicholas Bogel-Burroughs and Jeremy W. Peters, ‘You Have to Disobey’: Protesters Gather to Defy Stay-at-Home Orders, Associated Press, April 16, 2020). However, the events were widely interpreted as a minority view, dangerous to public health and public good. In the case of Ontario Canada, the Premier Doug Ford dismissed the protestors as unintelligent, immoral and “a bunch of yahoos.” (Ryan Rocca, “Bunch of yahoos’: Doug Ford blasts Toronto protest against coronavirus-related restrictions Global News, April 25, 2020) Facebook subsequently removed a number of posts attempting to organize similar events. Brandy Zadrozny, “Facebook removes some events calling for protests of stay-at-home orders” NBC News April 20, 2020)
It is unsafe to protest in public space, there is little sympathy for those who attempt it and considerable backlash, and the means of organizing gatherings is being restricted by the public platforms in the time of COVID 19?
We began the project by asking: In reaction to this crisis, can we take social movements online?
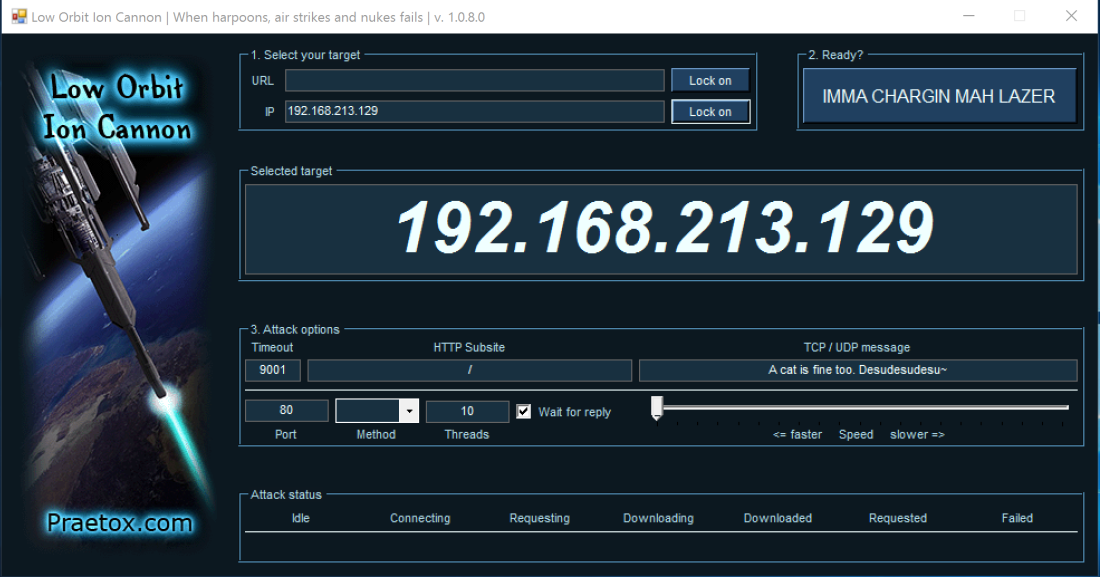
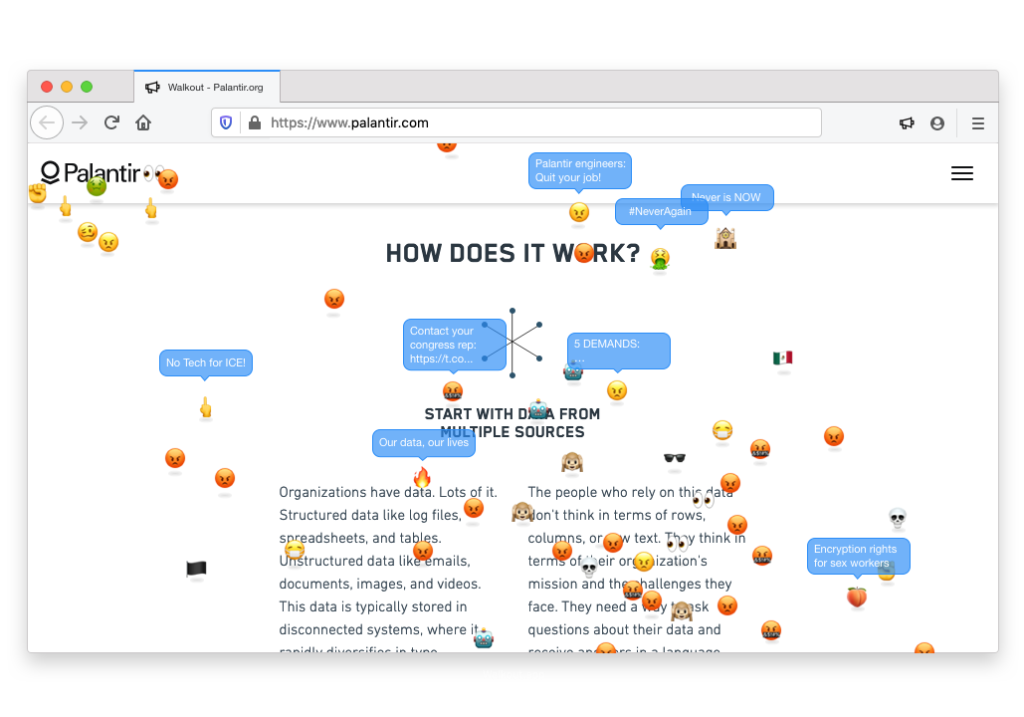
The original concept was to create an app called “Walk Out” which mimics a real-life street protest online in some ways. When starting the app, users would be required to fill two pieces of information: the domain name they would like to target, and an avatar or emoji to represent their presence online. The app would load the URL entered, and this page becomes the protest space. The page would be augmented as a chat room populated with other individuals represented by free-floating emojis. Every participant could move around, chat with their neighbors, write slogans and amplify those written by others. This activity would generate traffic against the targeted website. But beyond mere disruption, it would create a space where deliberation and a sense of communion is possible. The drawback to this is that it may be too similar to a Denial of Service Attack (DDos) under US and state law.
In 1994, the Computer Fraud and Abuse Act (CFAA) was amended to make it a crime to cause “the transmission of a program, information, code, or command to a computer or computer system” and damage a computer, network, data, information, or a program. This section applies to DDoS attacks which involve transmitting a code used to turn computers into zombies, and code directing zombie computers to hit a site, which causes the denial of access. (Brenner, S. Cybercrime and the Law pp 49-50)
Two states, Ohio and South Carolina statutes criminalize the act of preparing to commit a DDoS attack event if the act itself is never carried out, although neither state has applied the law yet. (Brenner, S. Cybercrime and the Law page 52)
Nevertheless, those prosecuted for DDoS attacks face potentially high sentences and have been convicted. Anonymous activists were sentenced to several years in federal prison and hundreds of thousands in damages, for running DDoS tools for less than a minute. An attack known as Operation Payback resulted in 14 individuals being charged under the CFAA. Potential sentences for DDoS actions in the US are high compared to other crimes and especially compared to other types of traditionally recognized activist activities: a sit-in would typically result in charges of trespass, if anything. (Mols Sauter, The Coming Swarm, 2014)
The other issue to consider with such an app is that it is limited – only people accessing the website and the owners of the website are aware of the protest. One criticism of DDos attacks that also applied to this concept is that the site being targeted may not have a direct relationship to the problem advocates wish to address.
Finally, contemporary web technologies mitigate the risk of denial of service. So much so that it would be impossible to generate any disruption without artificially amplifying the traffic generated by a DDoS, which would cross a legal and ethical line. In the introduction to the Coming Swarm, Ethan Zuckerman asks: if there is no public space on the Internet that forces us to hear voices we would normally choose not to hear, how can facilitate dissent and uncomfortable conversations? (Ethan Zuckerman in Mols Sauter, The Coming Swarm, 2014)
Research and Consultations
No member of our group considers ourselves an activist, and we explored academic and news sources exploring activism and social dynamics including: Gabriella Coleman, Hacker, Hoaxer, Whistleblower, Spy: The Many Faces of Anonymous (2014); Doug McAdam, Recruitment to High-Risk Activism: The Case of Freedom Summer American Journal of Sociology 1986 92:1, 64-90; Evgeny Morozov , To Save Everything, Click Here: The Folly of Technological Solutionism (2014); Clay Shirky, The Political Power of Social Media Foreign Affairs January/February 2011; Malcolm Gladwell and Clay Shirky “From Innovation to Revolution: Do Social Media Make Protests Possible? Foreign Affairs March/April 2011; “Gladwell vs. Shirky: A Year Later, Scoring the Debate Over Social-Media” Wired (December 27, 2011).
The literature does not offer a recipe for online activism, but a divergency of methods which range in legality, legitimacy, and effectiveness. Social media can be used for organizing for real world actions, conversely, move real world movements completely online – as is the case Hong Kong, where Grand Theft Auto V became the battle ground. (Isaac Yee, “Grand Theft Auto V becomes latest battleground of Hong Kong protests” CNN Business December 27, 2019)
Zeynep Tufecki’s book Twitter & Tear Gas is enlightening on this last point, in two ways. First Tufecki acknowledges that digital tools are great at amplifying movements in their most visible phase, but because they afford to skip decade-long movement building work, they also make social movements more fragile and less resilient. Second, the book highlights how digital tools are not mere standalone tools of amplification, but can also provide support during the many, diverse stages of a social movement (from shared awareness to logistics, to mobilization and deliberation). The use of digital tools must be done in conjunction with a myriad of other tactics/tools.
For the project it raised questions of what problem we are trying to solve and for whom? Would we design for a specific group? At what stage of social organizing is online most useful? Is it the near the beginning, where those with a common cause are seeking each other out? Or for those at a more organized stage, where they are already involved in social activism as a group?
To get specific ideas and feedback there was a need to approach activists who have been operating recently but shut down by the pandemic, which included Yellow vests in France and Hong Kong protesters, movements in India and Indigenous activists #IdleNoMore #ShutDownCanada and Families of Sisters in Spirit (a group dedicated to drawing attention to Missing and Murdered Indigenous women who use the acronym and hashtag #MMIW.) Ultimately for time and practicality, the Indigenous groups were chosen.
Missing and Murdered Indigenous Woman (MMIW)
This group has changed names throughout the years, known first as Stolen Sisters, later as Sisters in Spirit, but commonly associated or known by the acronym MMIW or MMIWG (where the G adds girls). The movement began in Canada in the early 2000s in BC, when young women, mostly Indigenous with the sex trade began to go missing in Vancouver BC and female hitchhikers disappeared along a 725-kilometre corridor of Highway 16 that connects Prince George and Prince Rupert, British Columbia. This has been dubbed ‘the highway of tears.” Families of the missing and murdered began to suspect that a serial killer could be at loose. They had little support from the police or media, so began organizing a series of vigils and marches to create pressure. Amnesty International and a Indigenous lobby group, Native Woman of Canada Association (NWAC) became involved and began tracking disappearances of Indigenous women across Canada and the solve rate of cases. The number documented grew to an estimated 4,000 missing or murdered women, generated media attention and led to provincial inquiries in BC (2010-2013) and Quebec, plus a National Inquiry. It was determined that the rate of homicide for Aboriginal females was almost seven times higher than other females, and were far more likely than other women to go missing.
Red dresses were a meme associated with the movement in Canada. As the movement spread to the US, the meme changed to handprint over the mouth, combining traditional face-painting with an image of silencing. The colour red may evoke the image of blood, but those within the movement say red was chosen based on traditional knowledge that it is the colour spirits can see.
In the US the movement is still gaining grounds and working to create political will to address apathy toward the conditions causing violence and justice for victims. In Canada the movement strangely stalled after the Inquiry report. Families received some compensation; however many are still frustrated by cases that remain unsolved and little news of any progress on the 231 recommendations of the National Inquiry. Canada is supposed to develop an action plan by June 2020.
#IdleNoMore
Idle No More is a grassroots protest movement, founded in October 2012 by four women: three First Nations women and one non-Indigenous. It began with teach-ins, then direct action. The original target was a piece of omnibus legislation known as Bill C-45 which included provisions to deregulate environmental protection on waters, and to make it easier to surrender reserve lands for development. Indegenous people understood both provisions to be an attack on treaty rights and actioned without consultation of Indigenous peoples as required by Treaties. Hundreds of protests in the form of round dances, marches beginning in November 2012. They continued after the government passed Bill C-35 into law in December 2012, but road and railway blockades and hunger strikes were added to the actions. There was a cooling down after January 11, 2013 when Prime Minister Harper met with a small number of elected First Nation leaders and promised to work on addressing some of the issues raised. #IdleNoMore then returned to its original form of teach-ins and education until January 2020. At that time #IdleNoMore resurfaced publicly in the form of marches, protests and blockades to support traditional chiefs in a remote BC community, Wet’suwet’en. The traditional chiefs have opposed construction of a pipeline across their territory for years, but in January the RCMP, Canada’s federal police force, were sent in to execute an injunction to remove their long-standing blockade so that construction could proceed.
#ShutDownCanada
#Shutdown Canada is closely related to #IdleNoMore. It arose in January 2020 and is more emblematic than official in its differentiation. Those using the hashtag #ShutdownCanada were engaged in and advocating blockades of railways and highways and favoured these actions over marches and less disruptive expressions of discontent.
Feedback from selected activist groups
The organizer of Sisters in Spirit Eastern Canada, a branch of the MMIW movement was contacted. She felt that their issue had been forgotten, police investigations of MMIW had not picked up, and that government was no longer communicating with families as to what actions it would implement from the inquiry: “I am still fighting for justice Karen [sic] ❤ National Inquiry did not help families with Closed Cases. It’s been so triggering with all this police violence going on…Only families who testified got $3500 for healing…what about the rest ?” While she expressed a need to recapture media attention and apply pressure on police; she did not see how social media could help.
An artist who has been active on several Indigenous issues including MMIW, Child Welfare and IdleNoMore appreciated the idea of online protests but did not think they were effective as they had no teeth. Looking at the proposal she commented: “I don’t think I have anything at this point to add. This isn’t my area of expertise and I personally find limits in online protests but that seems to be where humans are headed in general. Looking forward to when people can get out again.”
Others within the #IdleNoMore movement have expressed concern that while public posting and sharing on social media such as Facebook and twitter has been key to recruitment and organizing actions, it also allowed police to monitor their movements and create profiles of key advocates. Andrew Crosby and Jeffrey Monaghan, two Ottawa-based researchers used access to information requests to collect thousands of pages of government communication and police surveillance of IdleNoMore. When IdleNoMore resumed direct action in January 2020 they tried organizing by phone, asking individuals to volunteer to contact others on a 30-member call list to keep them informed of actions in an attempt to recruit out of the public eye. The concern surrounding the need for privacy from police surveillance and counter movements; while also needing a broad platform to recruit and build alliances has also been expressed by other advocacy groups.
A person connected to #ShutDownCanada named their biggest challenge as the moment where police move in to arrest those taking direct action. As actions go one, people tend to disperse leaving a small group to carry on a blockade. Very specifically he imagined an app that would alert everyone in the community to rush to the site when there is danger, violence or police action. The idea that the app could be used to alert people to other dangers like a robbery or an assault on a female was also suggested. “It should send out a notification to everyone within a certain radius who could respond quickly. Maybe first second third wave response graduating out in distance.” After some research it was determined an app that fulfills most of these requirements already exists.
Problem statement:
We found some commonalities among the groups, but particularly the issue impacting #IdleNoMore regarding communication. Activists are using public social media channels to organize and recruit others to their cause, but working in public also alerts the institutions they are rallying against to their plans. Essentially what they need is a private conversation in a public space, a way to alert select people to an action.
How might we create a means for activists to have a broad reach in organizing and recruiting supporters on the social media platforms. Could this communication also disrupt public space and create curiosity that would aid recruitment, and possibly draw media attention?
Solution
Concept: Code Talker
We created a plug-in that uses Facebook, which is the social media platform most preferred by the groups we consulted for organizing events. The plug-in allows the user to post a message that is encrypted on their public Facebook page. Only those others who also have the app installed and who are selected as friends by the original poster can see the decoded message. Everyone else sees only the encryption. To gain access, people download the application, and use its interface to add contacts and share content.
While encryption tools usually focus on private conversations, Code Talker introduces a degree of privacy in open Facebook conversations. It decouples people’s content from the platform where it is hosted, as encryption happens right before a message is posted. Besides, it uses the encrypted message as a viral vector, by including a short prompt that invites non-users to join the conversation by downloading the tool.
Under the hood, Code Talker relies on attribute-based encryption, a generalized version of public-key encryption. While public-key encryption is suitable for one-to-one conversations (e.g PGP, Signal), it is not viable for the kind of conversations people have on open social media platforms: among many issues, maintaining knowledge of contacts’ identities is cumbersome, and newly added friends can’t access content retroactively. In contrast, attribute-based encryption offers granularity in levels of trust between contacts, and backward data access. In the past, researchers have implemented attribute-based encryption systems applied to social media platforms, but they were assuming the platform would play along. In our case, we use this technology in an adversarial way.
We called the app Code Talker, after a term used in WWII when Indigenous soldiers spoke their language over military phone and communications devices to transmit secret messages. This kept enemy forces from intercepting messages. Their language was thought to be code, and the Germans called it ‘the unbreakable code.’ The soldiers were called ‘code talkers.’ For this prototype, we used the Navajo Code Talker military patch as reference for the application’s visual identity.

Use scenario
As monitoring peaceful protests and increasing criminalizing activities that were once allowed has become an issue in Canada since 9-11 (Paul Weinberg, “Policing of dissent, from the G20 to the Wet’suwet’en dispute” in CCPA pp 29-35) where the activists work the need for privacy in organizing has increasingly become a concern. It is a concern that is shared by other groups, for example protesters in Hong Kong could equally benefit from this type of application.
So for example IdleNoMore who regularly used Facebook to post messages, turned instead to a phone system in January when they began to organize support for Land Protectors in on unceded Wetʼsuwetʼen land in British Columbia, Canada. They organized ‘callers’ to keep 30 other activists notified, individually, by phone or text as to activities. This was an attempt to reach people without being monitored.
Indigenous activists will be able to transmit messages to each other using the public space; which is important to attract attention of other like-minded people for recruitment. It also offers some security against authorities or the establishments they are targeting intercepting or monitoring the content of the messages.
Now, with Code Talker they could post the event on their Facebook Page, reaching more people more efficiently in a public space, but keeping all details out of the public eye; revealing the messages only to those they trust.
In disrupting the public online space Code Talker also generates attention, media and others who follow high profile activists will know an action is being planned, and this will attract curiosity whether or not the content of a message is made available to them.
Next steps & Challenges
Indigenous activists will be able to transmit messages to each other using the public space; which is important to attract attention of other like-minded people for recruitment. It also offers some security against authorities or the establishments they are targeting intercepting or monitoring the content of the messages.
Feedback suggested adding a provocative image or meme to the coded text to make it more eye catching and intriguing. We’ll work on incorporating this idea.
Ethical challenges
We will need to be attentive to the risks users might face, so we can provide them with clear, actionable information. Just like in their real life counterparts, participation in online protests carries risks and requires well-informed decisions from all parties involved. For example:
- Someone may crack the encryption. A key may be given to someone who should not have it. We need to warn users that they should still be thoughtful about what they are sending as nothing is 100% secure.
- This may violate Facebook’s terms of agreement, and as a result if they do not like what the plug in is doing, they may kill it or suspend accounts. We need to warn users that this could happen. It is our hope it will not, or that it proves useful enough to Facebook’s users that the company accepts it.
Another consideration is that Code Talker could be used by groups with malevolent intent, such as white nationalists, terrorists or extreme” tactics by protestors – for example, blocking traffic, vandalizing property. However, because it only works in a public space, is designed to attract attention, and other software offers more private forms of communication, we feel the design of the App will be a deterrent for such users.
Code talker is envisioned for activists to whom disruption is the greater goal. As noted by Mols Sauter in The Coming Swarm (2014), for a protest action to attract sympathetic media attention, it must however look like what the media expects a protest action to look like. If such a tactic is seen as illegitimate (for example the way the media interprets DDoS attacks) the media could fail to recognize a given action as activism and cover only the novelty, spectacle, and criminality deployed.
Legal challenges
This project is rooted in civil disobedience, and we considered possible legal implications. Any program involving malware which introduces a contaminant into any computer, computer system, or computer network is criminalized under Federal and State U.S. law.
Denial of services (DDOS) attacks are criminalized under the Computer Fraud and Abuse Act, and individual states also have laws which criminalize DDOS attacks and other cybercrimes by criminalizing code that is designed to modify, damage, destroy, record, or transmit information within a computer, computer system, or computer network without the intent or permission of the owner of the information or the use of zombie computers. (Brenner, S. Cybercrime and the Law pp 41-49)
Code Talker may ultimately be found to violate the Facebook Terms of Service, however it does not seem to violate the current terms of service which only prohibit unlawful, misleading, discriminatory or fraudulent or viruses or malicious code or do anything that could disable, overburden, or impair the proper working or appearance of Facebook products. (see Facebook Terms of service)
Technical
Because it operates in a hostile environment — Facebook’s user interface, Code Talker faces several technical and security challenges.
First, it is threatened by the HTML obfuscation that Facebook uses to make scraping difficult on their website. This risk is thankfully alleviated by their compliance with the W3C’s Accessible Rich Internet Applications specification, which makes their HTML pages somewhat readable by software that’s designed with resilience in mind.
Second, because Facebook decides how content gets displayed, we can’t rely on mere scraping to identity and validate contact requests. This means we need to implement an external contact verification system that validates users are the legitimate owners of their Facebook accounts, via email or timestamp pictures.
Third, and most insidiously, Facebook’s ability to deprioritize content that appears programmatically manipulated might limit the flow of encrypted conversations.
Practical
Other significant challenges are the practical ones: successor systems inherently add a layer of complexity on existing interfaces. In our case, adding a degree of privacy to Facebook will add some friction to people’s user experience. For instance people might have to download a CodeTalker app to replace their Facebook app on mobile devices. Will these frictions deter people from using the tool altogether? What online rituals might we break? How about people who can’t use Code Talker and might end up being marginalized because they can’t read their communications anymore?
Selected Bibliography
Brenner, S. (2012). Cybercrime and the Law: Challenges, Issues, and Outcomes. Boston: Northeastern University Press.
Coleman, G. (2014). Hacker, Hoaxer, Whistleblower, Spy: The Many Faces of Anonymous.
Mcadam, D. (1986). Recruitment to High-Risk Activism: The Case of Freedom Summer. American Journal of Sociology, 92(1), 64-90.
Sauter, Molly (2014). The Coming Swarm. Bloomsbury Academic.
Schwartz, M. (2011). PRE-OCCUPIED. The New Yorker, 87(38), N/a.
Waisbord, S. (2018). Twitter and Tear Gas: The Power and the Fragility of Networked Protest. Social Forces, 96(4), E3.